Bypassing CSP by Abusing JSONP Endpoints
This blog post discusses a technique that can be used to bypass CSP (Content Security Policy).
Background #
What is CSP? #
“Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross Site Scripting (XSS) and data injection attacks. These attacks are used for everything from data theft to site defacement or distribution of malware.” — Mozilla Developer Documentations.
What is JSONP? #
JSON with Padding (JSONP) is a technique used to request and retrieve data from a server without worrying about cross-domain, bypassing the Same-Origin Policy (SOP).
The Attack #
The concept works as the following:
JSONP APIs typically work by having a parameter that sets a callback so that users of the JSONP API can freely use the API according to their code.
The GET parameter is reflected in the response in the 0 offset. This means that we control the start of the response body. JavaScript Magic
JavaScript is a very dynamic language. It dynamically allows us to do many things we should not do and are not supposed to do.
Let’s use some JavaScript magic on our side here.
What if we enter:
alert(1);//
As our callback?
If no proper sanitization is done on the JSONP endpoint, it will be reflected as the following:
alert(1);//{"name": “Mazin"}
This is technically a correct JavaScript code!
The syntax is correct, as the rest of the response is commented. JS engines would treat the data as a typical JavaScript code instead of a JSONP endpoint.
So, importing the JSONP callback via a script tag as the following:
<script src="http://example.com/jsonp?callback=alert(1);//"></script>
This will result in the following:
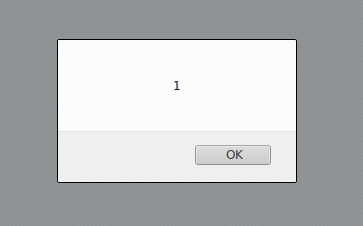
Let’s say that we have the following CSP policy on a website:
Content-Security-Policy: default-src 'self'
This policy blocks anything that does not load from within the exact origin.
Since, according to the browser, this JavaScript code is hosted on the domain, we can use it to bypass the Content Security Policy. We can craft the payload to contain our payload, followed by a comment commenting on the rest of the response. When importing the URL via <script> tag, it would be treated as the content of the JavaScript code.
So, for example, if twitter.com has an XSS, and there is a white-listed domain on the CSP rule called “example.com”, and this domain holds a JSONP endpoint, then the CSP policy for twitter.com will be bypassed by abusing the JSONP endpoint for example.com.
What to Do? #
Developers That are Responsible for JSONP endpoints #
Restricts the callback name to specific keywords or disallows non-alphanumeric from returning within the response. Furthermore, it would be best to consider protecting against the Rosetta Flash exploit.
Penetration Testers #
Whenever you face a Content Security Policy on an application, review all white-listed domains and search for JSONP endpoints.
Blue Teams #
Review your white-listed domains for domains that hold JSONP endpoints. This can be a bypass for your CSP policy.