Session Hijacking in Instagram Mobile App via MITM Attack [0-DAY]
- 2 minsIn this post, I will share a new critical issue I identified on Instagram Mobile App. During my tests on their Android app, I set up a lab to pentest the app. Then, I started using the app on my phone and monitoring the traffic in the network using Wireshark, looking for evidence of unencrypted data that goes through the network or a technique to make this data unencrypted (if it was encrypted). As soon as I logged into my account on my phone, Wireshark captured unencrypted data that went through HTTP. This data includes The pictures the target is watching, the target’s session cookies, the username, and the ID.
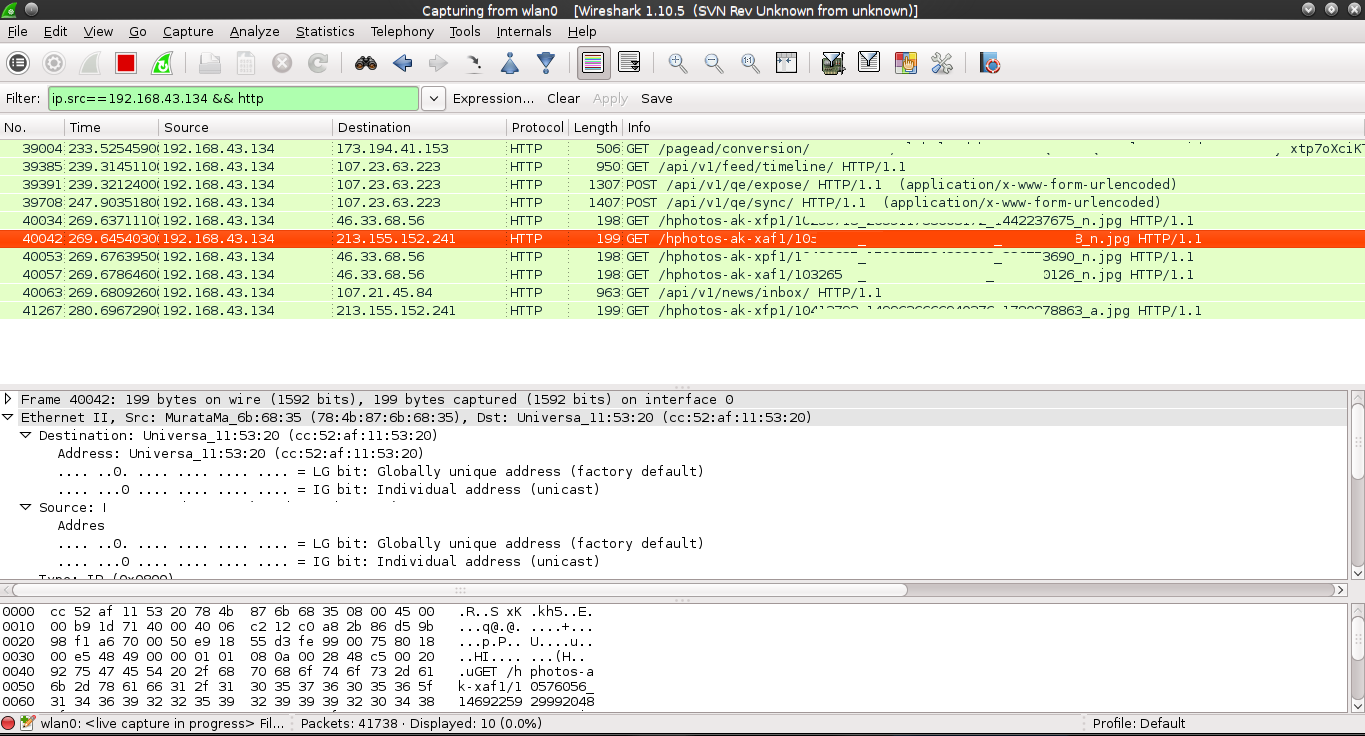
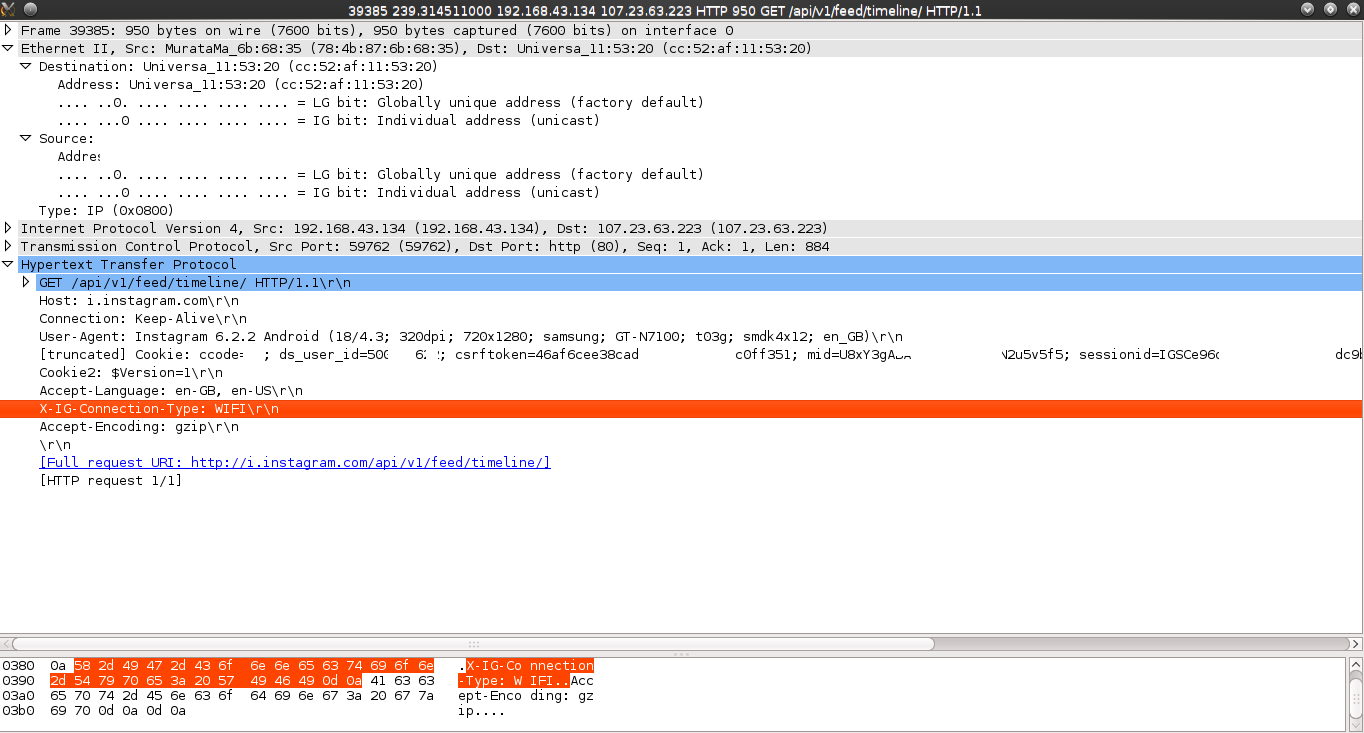
I was shocked after seeing the results, and it is unbelievable that Facebook, the company responsible for Instagram, did not ensure that the data is secured and goes through HTTPS.
I took the session cookies and used them on my computer. It worked successfully.
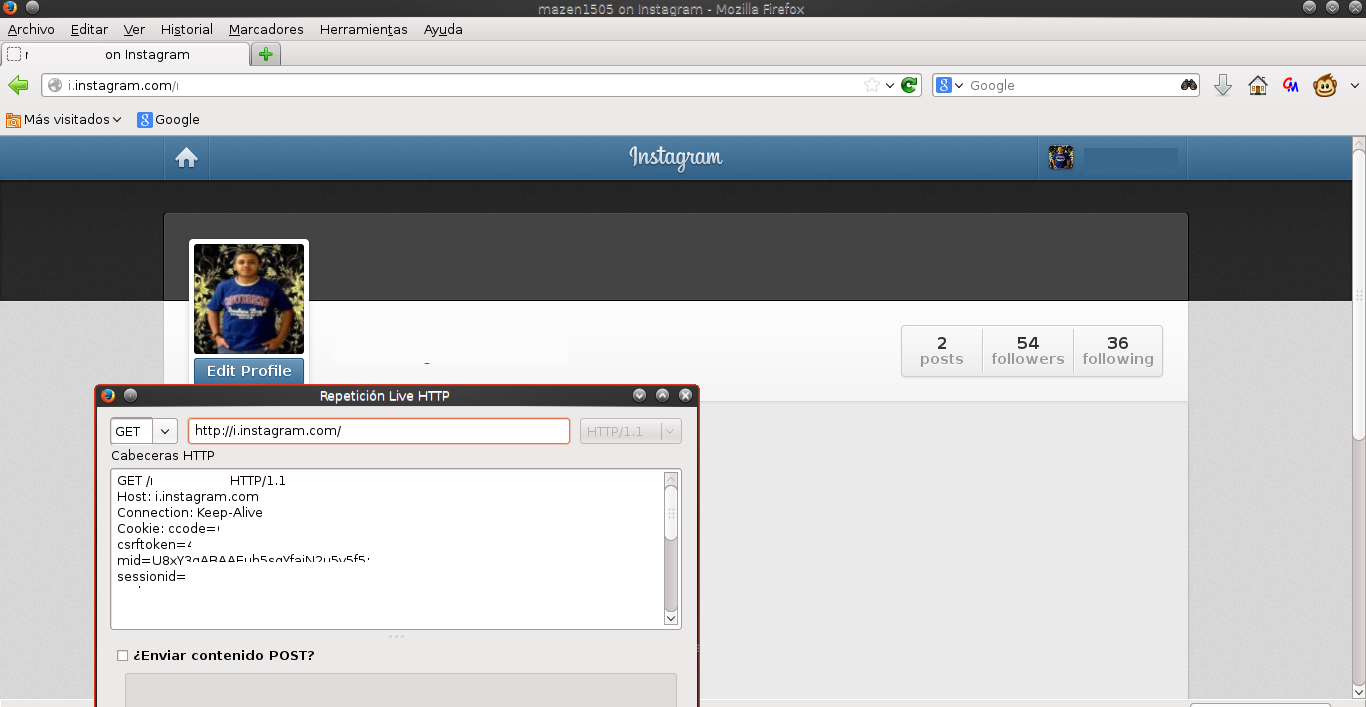
I have reported this issue to Facebook, and they responded with the following:
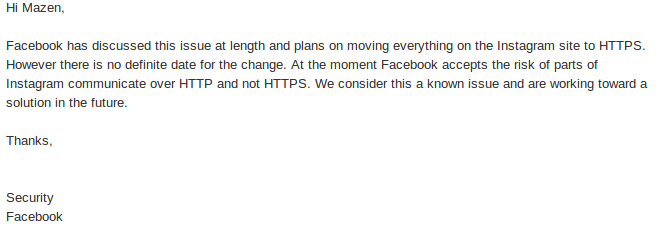
The security member of Facebook stated: “Facebook accepts the risk of parts of Instagram communicating over HTTP, not over HTTPS.” If this unencrypted data can lead to session hijacking and stalking Instagram users, it’s a considerable risk.
Timeline:
- Jul 24, 2014, 4:35 am – Reported the issue.
- Jul 24, 2014, 4:38 am – Received a confirmation email of receiving the submission.
- Jul 24, 2014, 9:45 pm – Received the first response from Facebook Security.
- Jul 24, 2014, 9:45 pm – I Asked for a disclosure.
- Jul 24, 2014, 11:56 pm – Received the second response from Facebook Security.
Recommendation:
Until a patch is released (there is no specific date for releasing a patch that Facebook has assigned), do not use the Instagram mobile app; instead, use the typical website, which is generally secured and encrypted.
Final Thoughts
It is unbelievable that a company such as Facebook needs to take the maximum measures to ensure their users’ security. Right now, this issue might be exploited by threat actors, and users do not have a way to prevent it.
Related Posts
