Exploiting Misconfigured Apache server-status Instances with server-status_PWN
- 3 mins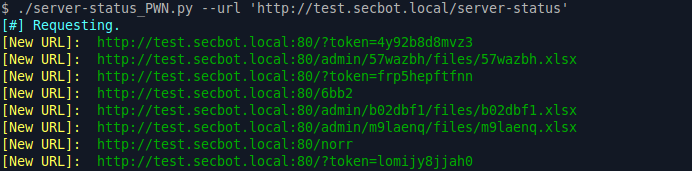
One of the things that my clients like in my work is that I always like to do my best in providing technical Proof of Concepts in findings I discover. This makes it easier for technical departments to reproduce the issues and is also an excellent way to show how bugs and issues can be exploited.
I recently had an assessment where I discovered several publicly exposed Apache server-status instances. If you are unfamiliar with Apache server-status, please read this document.
When I initially reported it to the company, the team thought it would be an acceptable risk to leave it there.
Apache server status should not be accessible, as it poses a significant privacy and security risk.
What information can be exposed?
-
All requested URLs by all Hosts/VHosts on the Apache server. This includes:
-
Hidden and obscure files and directories.
-
Session Tokens on GET REQUEST_URI (eg.. https://example.com/?token=123). If tokens are passed through the GET HTTP method, they will be exposed, regardless of SSL encryption.
-
All clients’ IP addresses, along with URLs the clients have requested.
What do we need as attackers?
We need a script that constantly monitors the exposed Apache server-status, extracts all new URLs, and saves them for later testing.
Also, if we are performing an intelligence engagement, we would need all IPs that interact with the Apache server that hosts our target website and the requested URLs. Then we need to monitor the service on the hour constantly.
What have I done to solve the issue?
As a penetration tester, I believe that without an actual PoC, the attack would be theoretical, simple as that. PoC || GO is the rule of the game.
So, I wrote server-status PWN.
Introducing server-status PWN
Server-status PWN constantly requests and parses Apache server-status pages for any new event. Whenever a unique URL is requested, or a new client IP address is used, it will be logged and reported. It outputs the logs in a SQLITE3 database.
Example Tool Output:

server-status_PWN Homepage: https://github.com/mazen160/server-status_PWN
[February 20, 2017] Update:
The Apache Foundation has changed their official Apache server-status instance, available at https://www.apache.org/server-status.
Initially, it was publicly and intentionally accessible. It shows a large notice stating that the data is “static data” and does not hold any users’ data or information.
Screenshot