W3 Total Cache's W3TotalFail Vulnerability That Leads to Full Defacement (CVE-2014-9414)
- 4 minsIn this post, I will be talking about a critical vulnerability that affects W3 Total Cache, the most popular WordPress plugin in the world. Most major companies use W3 Total Cache, which provides a vital service that every WordPress website needs.
Overview on W3 Total Cache
“W3 Total Cache improves your site’s user experience by increasing server performance, reducing the download times, and providing transparent content delivery network (CDN) integration.”
- source: https://wordpress.org/plugins/w3-total-cache/
After I downloaded the plugin (v0.9.4) on my testing WordPress site, I started testing it for less than 15 minutes. I noticed a CSRF token called “_wp_nonce” during that duration, so I started checking for bugs. I have seen that the CSRF token is not being validated, and no additional methods are used to prevent CSRF issues. So, by deleting its value from the request, a successful CSRF attack can be performed.
Then, I started verifying the issue, and I was able to reproduce the same issue in all the plugin’s requests. After that, I started making scenarios on how the CSRF issue can be used to cause the most significant damage and the highest impact on W3 Total Cache users.
One of the features that W3 Total Cache provides is the ability to redirect user agents that contain a phrase mentioned in the plugin’s settings to a specified link. The feature is made so administrators can redirect users to the mobile version of the site or similar uses, for example. It’s a nice feature but an excellent feature for exploiting the bug and defacing websites.
I have researched to gather all the common phrases on most user agents. The research results showed that the following expressions are used on more than %97 of all user agents and %100 of all checked user agents.
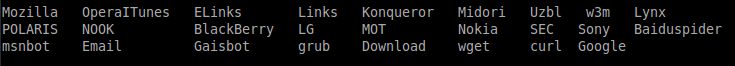
Then, I started writing an exploit for the issue. All authenticated WordPress users who load the exploit will set up a policy that all user agents that contain the previous phrases will be redirected to a malicious page. Because the terms I wrote exist on more than %97 of all user agents, everyone will be redirected to the attacker’s page using the exploit.
POC: http://packetstormsecurity.com/files/129512/W3-Total-Cache-0.9.4-Cross-Site-Request-Forgery.html
Demo Video_:
The following screenshot shows the response before & after using the exploit:
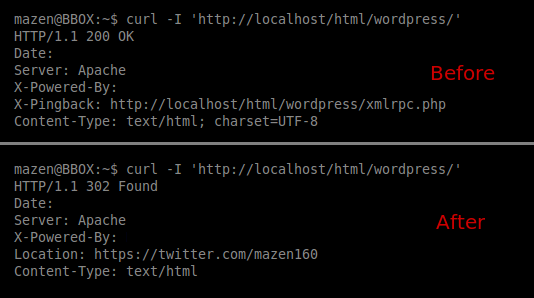
Steps to Reproduce:
1- An attacker posts a comment that contains a link to the exploit to the WordPress victim that uses W3 Total Cache
2- The victim opens the comments section and clicks on the link.
3- The exploit is loaded while the victim is authenticated with administration privileges.
4- Anyone who opens the victim’s website will be redirected to the attacker’s deface page.
Responsible Disclosure
I quickly contacted W3-Edge, the company responsible for W3 Total Cache, and the leading developer of the project, Fredrick Towns, contacted me asking about the details regarding the vulnerability that exists on v0.9.4, and he replied that the fix will be released soon (the patch has been released now).
Recommendations
Update to the latest version of W3 Total Cache (v0.9.4 is vulnerable, and all versions released before might also be vulnerable).
Summary
- W3 Total Cache v0.9.4 is vulnerable to a critical CSRF vulnerability that may lead to the full deface of users using the vulnerable plugin. Versions before 0.9.4 might be affected, too.
- The exploit can be used by researching all phrases used on most user agents.
- This issue is not complex to exploit and can be used to cause different impacts on WordPress users who are using a vulnerable version of W3 Total Cache.
- The W3TotalFail vulnerability is easy to exploit; any malicious user with little experience can use the vulnerability to cause significant damage and deface.
Final Thoughts
I didn’t expect to find a critical issue like this one in a popular plugin such as W3 Total Cache that easily. If that’s the condition of the most used Wordpress plugin, many vulnerabilities on Wordpress plugins might be publicly exploited by threat actors. Wordpress is secure by itself, but plugins have the most significant impact on Wordpress security. Users should be careful about what plugin they use and how much effort they put into securing it.
Some companies don’t care about their security; neither are professional in handling a security vulnerability. W3-Edge was one of them. When I reported the issue on October 7th, I expected that the W3-Edge team would be patching the issue quickly, but instead, their responses were unkind, and they were not cooperating with me. I have not appreciated that from them.
