My Story with Onavo (a Facebook's Acquisition)
- 1 minWhen I was checking the Facebook WhiteHat page, I realized that they added a new target to the scope: Onavo.
I downloaded their apps and started to intercept the links that I found.
One of the links raised an eyebrow. I said to myself that this looks vulnerable.
The link looks something like this:
http://cf.onavo.com/iphone/mc/deactivate.html?url=/somethingthatIforget/&seed=1394953248
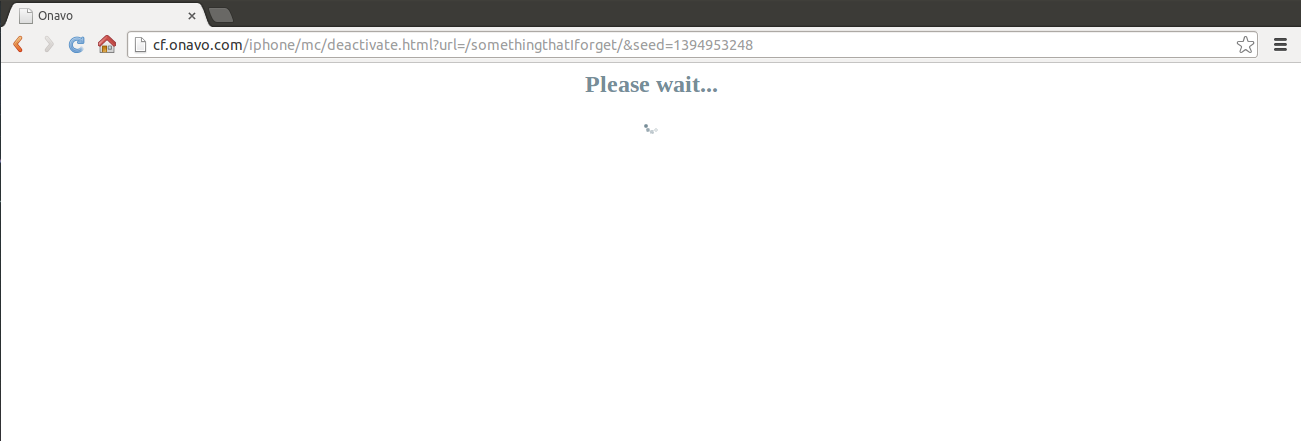
It seems vulnerable to Open Redirect.
I executed the link this:
http://cf.onavo.com/iphone/mc/deactivate.html?url=http://bing.com&seed=1394953248.
It redirected me to http://bing.com.
I have an Open Redirect vulnerability right now, but that’s not enough.
After digging up more on the nature of the page, I realized that it redirects me after about 2 seconds. So it looked something like this:
<meta http-equiv="refresh" content="0; url=http://bing.com/" />So I changed it to issue a redirection to
javascript:alert(document.domain)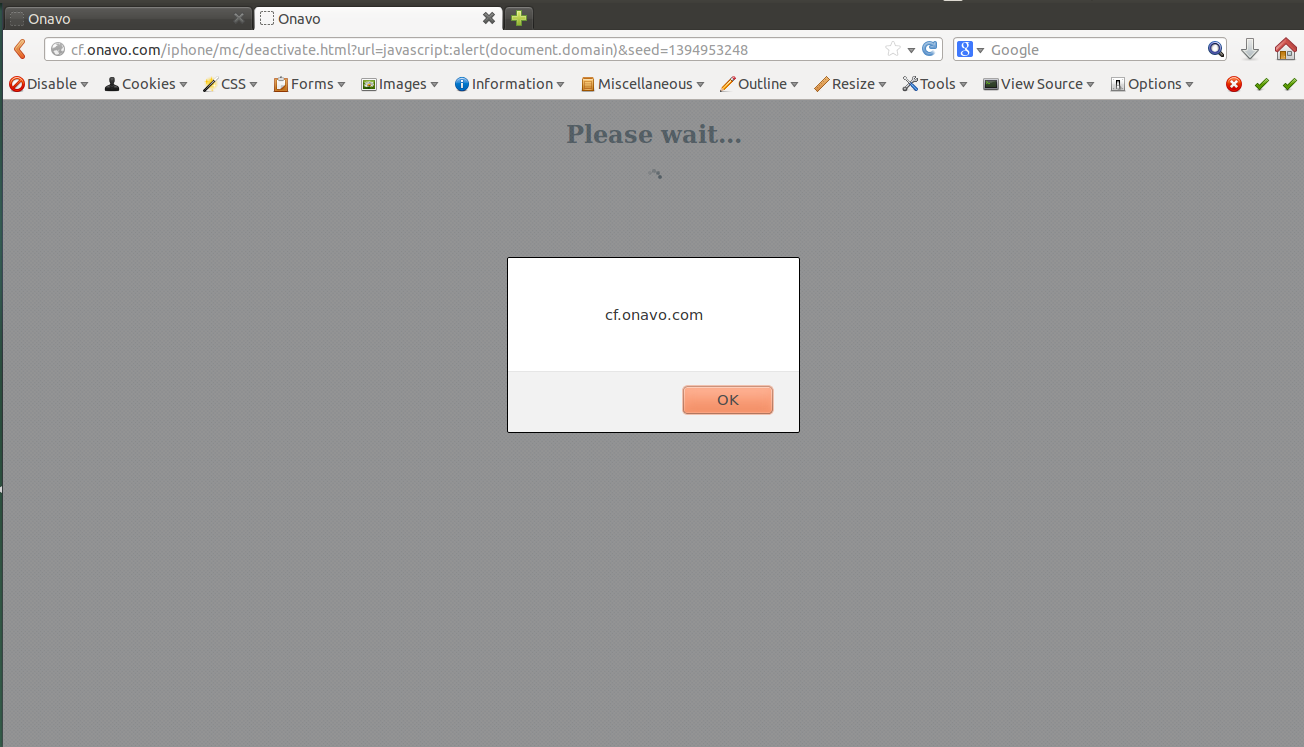
Timeline
- Mar 16, 2014 - Reported
- Mar 17, 2014 - Email from Saul of Facebook Security acknowledging the issue.
- Apr 30, 2014 - The issue seems fixed to me. I emailed Facebook asking them about the current status
- May 1, 2014 - Email from Saul of Facebook Security informing that the issue has been patched
- May 1, 2014 - Received a payment email from Facebook
Rewards
- Facebook WhiteHat of 2014 https://www.facebook.com/whitehat/thanks.
- Cash reward of $500.
Final Thoughts:
- Participating in bug bounties gives you experience in different locations and helps you build new ideas for security-related issues.
- If you have an open redirector vulnerability, you should test for XSS, too.
- Never give up.
Related Posts
- Google UI-Redressing Bug That Discloses The User's Email Address
- Bypassing Google Password Alert with One Line of Code
- Facebook Messenger Multiple CSRF Vulnerabilities
- W3 Total Cache's W3TotalFail Vulnerability That Leads to Full Defacement (CVE-2014-9414)
- Session Hijacking in Instagram Mobile App via MITM Attack [0-DAY]
